UNIT-2
1. What are sensors? Explain its working.
Ans:
Sensors are devices that detect and respond to physical phenomena, such as light, temperature, motion, pressure, and sound. They serve as critical components in various systems, particularly in the Internet of Things (IoT), where they collect data to monitor and control environments, processes, and devices.
Working of Sensors:
-
Detection: Sensors detect changes in the environment or specific stimuli. For example, a temperature sensor detects changes in temperature, while a motion sensor detects movement within a certain area.
-
Signal Conversion: Once the sensor detects a stimulus, it converts the physical quantity into an electrical signal. This conversion can happen in several ways, depending on the type of sensor:
- Analog Sensors: These generate continuous electrical signals that vary in voltage or current in proportion to the measurement being taken. For instance, a thermistor changes its resistance with temperature changes, providing an analog voltage output.
- Digital Sensors: These provide discrete signals that represent specific thresholds or states. For example, a digital temperature sensor outputs a binary signal (0 or 1) once the temperature surpasses or falls below a predefined limit.
-
Signal Processing: After the sensor generates an electrical output, the signal typically undergoes some processing. This can include amplification, filtering, and conversion from analog to digital signals (in the case of analog sensors) using Analog-to-Digital Converters (ADCs).
-
Data Transmission: The processed data is then transmitted to a microcontroller, computer, or IoT platform for further analysis. This transmission can occur through various communication protocols such as HTTP, MQTT, or Bluetooth, depending on the application.
-
Action Based on Data: Once the data reaches the processing unit, it can be analyzed and used to trigger actions. For instance, in a smart thermostat, temperature data collected by a sensor can be used to adjust heating or cooling systems accordingly.
Applications of Sensors:
- Environmental Monitoring: Sensors are used to monitor air quality, humidity, and temperature in different environments.
- Healthcare: Medical sensors detect physiological parameters such as heart rate, blood pressure, and glucose levels.
- Industrial Automation: Sensors monitor machinery performance, detect faults, and optimize manufacturing processes.
- Smart Homes: Motion and light sensors enable automation for lighting, security, and energy management systems.
2. What are sensors? How are they classified?
Ans:
Sensors are devices that detect physical properties or changes in the environment, converting these physical phenomena into measurable signals, typically electrical signals. They play a crucial role in gathering data for monitoring and controlling systems, especially in applications involving automation, IoT, and smart devices.
Classification of Sensors:
Sensors can be classified based on various criteria, including their working principles, output signals, and application areas. Below are some common classifications:
- Based on Working Principle:
- Active Sensors: These sensors require an external power source to operate and actively emit energy to measure a physical parameter. For example, radar sensors emit radio waves and measure their reflection to detect objects.
- Passive Sensors: These sensors do not require an external power source; instead, they respond to changes in the environment and convert that energy into an output signal. An example is a thermocouple, which generates a voltage output based on temperature differences.
- Based on Output Signal:
- Analog Sensors: These produce a continuous output signal corresponding to the measured parameter. For instance, a potentiometer varies its resistance continuously to measure position or angle.
- Digital Sensors: These provide discrete output signals (usually binary) representing specific states or thresholds. For example, a digital temperature sensor might output a signal only once a certain temperature is reached.
- Based on the Measured Parameter:
- Temperature Sensors: These include thermocouples, thermistors, and infrared sensors used for measuring temperature.
- Pressure Sensors: These measure the pressure of gases or liquids, such as piezoelectric or capacitive pressure sensors.
- Proximity Sensors: These detect the presence or absence of an object within a specified range, including capacitive, inductive, and ultrasonic sensors.
- Light Sensors: Also known as photodetectors, these measure light intensity, such as photoresistors (LDR) or photodiodes.
- Based on Application:
- Industrial Sensors: Used in manufacturing processes for monitoring equipment and quality control (e.g., strain gauges, flow sensors).
- Environmental Sensors: Employed to measure environmental parameters like air quality, humidity, and pollutant levels.
- Consumer Electronics: Found in devices such as smartphones, cameras, and smart home devices for features like ambient light detection and location tracking.
- Based on Technology:
- Capacitive Sensors: Work on the principle of measuring changes in capacitance to detect object presence or proximity.
- Resistive Sensors: Change their resistance based on a physical stimulus (e.g., temperature, pressure).
- Optical Sensors: Use light as a measurement source or indicator, used in applications like cameras and fiber optic sensors.
3. Explain any two sensors of your choice.
Ans:
Here are explanations of two commonly used sensors: Temperature Sensor and Ultrasonic Sensor.
1. Temperature Sensor
Description: Temperature sensors are devices that measure temperature and provide an output signal corresponding to the temperature level. They are widely used in various applications, including industrial processes, HVAC systems, and personal electronics.
Types:
- Thermocouples: These consist of two different metals joined at one end. When the junction experiences a temperature difference, a voltage is generated, which can be related to temperature. They are known for their wide temperature range and fast response.
- Thermistors: These are temperature-sensitive resistors whose resistance changes significantly with temperature. They are known for their high sensitivity and accuracy within a limited temperature range.
- Resistance Temperature Detectors (RTDs): These sensors provide high accuracy and stability. RTDs use the principle that the electrical resistance of certain metals changes with temperature.
Applications:
- HVAC Systems: Used to control heating and cooling devices based on room temperature readings.
- Food Safety: Monitoring and controlling the temperature in refrigeration to ensure food safety standards.
- Medical Devices: Used in thermometers and patient monitoring systems to keep track of body temperature.
2. Ultrasonic Sensor
Description: An ultrasonic sensor uses ultrasonic waves (sound waves with frequencies above the human hearing range) to detect objects and measure distances. The sensor emits ultrasonic pulses and listens for the echo as these waves bounce back from the nearest object.
Working Principle:
- The sensor emits a burst of ultrasonic sound waves.
- The waves travel through the air until they hit an object.
- The waves reflect back to the sensor.
- The sensor measures the time taken for the echo to return and calculates the distance to the object using the speed of sound.
Applications:
- Obstacle Detection: Commonly used in robotics and automotive applications for collision avoidance systems.
- Distance Measurement: Utilized in level sensing applications (e.g., measuring the level of liquid in tanks).
- Automated Parking Systems: Helps in alerting drivers to the proximity of nearby objects when parking.
4. Tabulate the differences between Analog sensors and Digital sensors.
Ans:


5. What is meant by actuators used in IOT devices? What are their types?
Ans:
Actuators in IoT Devices:
Actuators are devices that convert electrical signals (either from sensors or controllers) into physical actions. They are key components in IoT systems, allowing for the movement or operation of devices in response to received data or commands. Actuators play a crucial role in automating processes by manipulating physical systems based on the information provided by sensors or control units.
Types of Actuators:
- Mechanical Actuators:
- Description: These actuators convert electrical energy into mechanical energy. They are commonly used to create motion.
- Examples:
- Motors (AC and DC): Used to drive wheels in robotic applications or open/close valves.
- Solenoids: Used to pull or push mechanisms (e.g., door locks).
- Hydraulic Actuators:
- Description: These actuators use pressurized fluid to create motion. They are typically used for heavy-duty applications requiring significant force.
- Examples:
- Used in industrial machines, excavators, or any application that requires lifting heavy loads.
- Pneumatic Actuators:
- Description: These rely on compressed air to generate movement. They are popular in applications requiring rapid action and high speed.
- Examples:
- Used in automated assembly lines, box compactors, and in robotics.
- Thermal Actuators:
- Description: These actuators use changes in temperature to create motion. They typically consist of materials that expand or contract with temperature changes.
- Examples:
- Used in thermostats or valves that open/close based on heat.
- Stepper Motors:
- Description: These are a type of motor that moves in discrete steps, allowing precise control over position and speed.
- Examples:
- Used in printers, CNC machines, and robotics where precise control of position is necessary.
- Servo Motors:
- Description: These motors are combined with a feedback system (like a potentiometer or encoder) that allows precise control over angular position, velocity, and acceleration.
- Examples:
- Commonly used in robotics, aircraft control surfaces, and RC vehicles.
- Electromagnetic Actuators:
- Description: These use electromagnetic fields to create motion or changes in a mechanical system.
- Examples:
- Used in relays and in applications where switching electrical signals are required.
6. Write a short note on HTTP protocol used in IOT devices.
Ans:
HTTP Protocol in IoT Devices
Hypertext Transfer Protocol (HTTP) is a foundational protocol used for transmitting data over the World Wide Web. In the context of IoT (Internet of Things), HTTP plays a crucial role in enabling communication between IoT devices and servers, allowing for the exchange of control commands and data.
Key Features of HTTP in IoT:
- Request-Response Model:
- HTTP operates on a request-response model, where an IoT device (client) sends a request to a server (or another device) and receives a response. This model facilitates straightforward communication, making it easier to develop web-based interfaces for IoT applications.
- Stateless Protocol:
- Each HTTP request from a client to a server is treated as an independent transaction. The server does not retain information about the client's previous requests. This statelessness simplifies server management but can require additional mechanisms (like session IDs) for maintaining state across multiple interactions.
- Data Formats:
- HTTP supports various data formats for communication, primarily JSON (JavaScript Object Notation) and XML (Extensible Markup Language), which are both widely used in IoT applications for data exchange due to their lightweight nature.
- Ease of Use:
- HTTP is well-understood and supported by many platforms and devices, making it a popular choice for developers working on IoT applications. Its broad compatibility with existing web technologies facilitates integration with cloud services, APIs, and web interfaces.
- Secure Communication:
- With the introduction of HTTPS (HTTP Secure), which utilizes SSL/TLS, developers can ensure encrypted communication between IoT devices and servers, enhancing data privacy and security in IoT applications.
Applications in IoT:
- Remote Device Management: HTTP can be used for monitoring and controlling IoT devices remotely, allowing users to send commands to devices (like turning lights on/off) and receive status updates.
- Data Collection: IoT devices can use HTTP to push sensor data to cloud services for further analysis, visualization, or storage.
- Interaction with Web Services: HTTP enables IoT devices to interact seamlessly with various web services, facilitating actions like triggering events based on real-time data (e.g., sending alerts, notifications).
7. What is the CoAP protocol used for? List some of its applications.
Ans:
CoAP (Constrained Application Protocol) is a web transfer protocol specifically designed for use in resource-constrained environments such as IoT devices and networks. It is based on the principles of HTTP but is optimized for constrained nodes and networks, which means it has lower overhead and is more suitable for low-power and lossy networks.
Applications of CoAP:
-
Smart Home Automation: CoAP is often used for controlling and monitoring smart home devices such as lights, thermostats, and door locks due to its lightweight nature.
-
Smart Metering: It enables communication between smart meters and central systems for energy monitoring and management, allowing real-time data collection and management.
-
Healthcare Monitoring: CoAP can be used in remote health monitoring systems where medical devices send data to healthcare providers or applications for analysis and alerts.
-
Industrial Automation: In industrial settings, CoAP can facilitate communication between sensors and control devices, helping to monitor processes and enable automation.
-
Environmental Monitoring: CoAP is utilized in applications such as weather stations and pollution monitoring, where sensors relay data back to centralized systems for analysis and reporting.
-
Smart Agriculture: It is used in precision agriculture applications, enabling sensors to monitor soil conditions and environmental factors, thereby optimizing irrigation and resource use.
These applications leverage the efficient data transmission and low power consumption characteristics of CoAP, making it ideal for diverse IoT scenarios
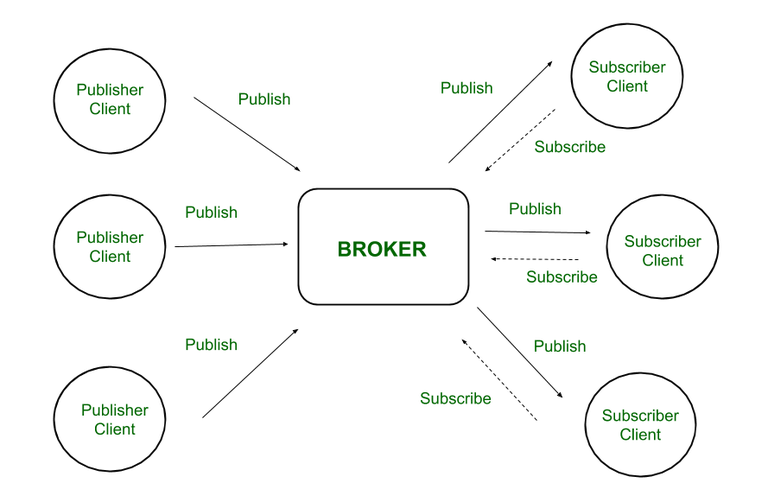
8. With the help of an illustrative diagram, explain the architecture and working of
MQTT protocol.
Ans:
MQTT (Message Queuing Telemetry Transport) is a lightweight messaging protocol designed for low-bandwidth, high-latency, or unreliable networks, commonly used in IoT environments. It operates on a publish-subscribe model, where devices can publish messages to a topic, and other devices can subscribe to those topics to receive the messages.
MQTT Architecture Components
-
Broker (Central Server)
- The broker is the central component that manages message exchange between clients.
- It receives messages from publishers and forwards them to appropriate subscribers based on topics.
- It ensures message delivery reliability and supports Quality of Service (QoS) levels.
-
Publisher Clients
- These clients send (publish) messages to the broker.
- Messages are sent under specific topics, which categorize the information.
- Publishers do not send messages directly to subscribers.
-
Subscriber Clients
- These clients subscribe to specific topics to receive messages.
- They rely on the broker to forward relevant messages.
- A client can be both a publisher and a subscriber.
Working of MQTT Protocol
-
Publishing Messages
- A publisher client sends a message to the broker under a specific topic (e.g., "home/temperature").
-
Message Handling by Broker
- The broker receives the message and checks which subscribers are subscribed to the topic.
- The broker then forwards the message to all interested subscribers.
-
Subscribing to Topics
- A subscriber client subscribes to a topic (e.g., "home/temperature").
- When a message is published under that topic, the subscriber receives it.
-
Message Delivery
- The MQTT protocol ensures message delivery with QoS levels (0, 1, 2), ensuring reliability depending on network conditions.
Key Features of MQTT
- Lightweight & Efficient: Ideal for IoT and low-bandwidth networks.
- Decoupled Communication: Publishers and subscribers do not communicate directly.
- Supports QoS Levels: Guarantees different levels of message delivery.
- Persistent Sessions: Retains client state for reconnection.
9. What is the XMPP Protocol? Explain its working.
Ans:
XMPP (Extensible Messaging and Presence Protocol) is an open-standard communication protocol based on XML (Extensible Markup Language) designed primarily for real-time messaging and presence information. Originally developed for instant messaging, XMPP has been expanded to support a variety of applications including IoT communications, social networking, and collaboration.
Key Features of XMPP:
- Real-time Messaging: XMPP is built for real-time exchange of messages, enabling instant communication between devices and users.
- Presence Information: It provides mechanisms for presence updates, allowing applications to know the online status of users or devices (e.g., online, offline, idle).
- Extensibility: It allows developers to create custom extensions through XMPP Extension Protocols (XEPs), which can add new functionalities without changing the core protocol.
Working of XMPP:
- Client-Server Architecture:
- XMPP operates on a client-server model. Clients (such as instant messaging applications or IoT devices) communicate through an XMPP server, which manages message routing and presence information.
- Establishment of a Session:
- An XMPP client initiates a session by connecting to an XMPP server and authenticating itself using credentials (username and password). This typically involves the exchange of XML stanzas.
- Sending and Receiving Messages:
- After establishing a connection, the client can send messages to other users or devices. Messages are sent in the form of XML stanzas, which are structured data packets formatted in XML.
- Each message contains sender, recipient, and content information.
- Example of a message stanza:
<message to='user@example.com' from='client@example.com'>
<body>Hello, World!</body>
</message>
- Presence Updates:
- Clients can send presence information to indicate their availability or status. This involves sending presence stanzas that specify the user's current state.
- Example of a presence stanza:
<presence>
<show>available</show>
<status>Online</status>
</presence>
- Message Routing:
- The XMPP server routes messages to the appropriate recipient based on the destination address specified in the message stanza. If the recipient is offline, the server can store the message until the recipient becomes available (if configured to do so).
- XMPP Extensions:
- Developers can use XEPs to add features such as file transfer, group chat, or even sensor data reporting in IoT applications. These extensions can enhance the basic functionality of XMPP.
Applications of XMPP:
- Instant Messaging: Originally designed for conversational purposes, XMPP is widely used in applications like Google Chat and WhatsApp.
- Collaboration Tools: Used in various collaboration platforms for real-time communication.
- IoT Communication: Suitable for communicating between devices in IoT networks, where real-time data streaming and presence information can be critical.
10. What are the various privacy and security issues that can arise in IOT devices?
Explain.
Ans:
The Internet of Things (IoT) devices have rapidly proliferated, creating convenience and improving efficiency across various domains. However, this explosion of interconnected devices also raises significant privacy and security concerns. Here are some of the key issues that can arise:
1. Data Privacy:
- Unauthorized Data Access: IoT devices often collect and transmit vast amounts of personal data. If these devices are not secured properly, unauthorized users may gain access to sensitive information.
- Data Breaches: Cyberattacks targeting IoT devices can lead to significant data breaches, exposing personal information such as health data, location, and usage patterns.
2. Weak Authentication:
- Insecure Default Passwords: Many IoT devices are shipped with default usernames and passwords, which users often neglect to change. This provides easy access for malicious actors.
- Lack of Strong Authentication: Many IoT systems do not implement robust authentication mechanisms, making it easier for attackers to compromise devices.
3. Inadequate Encryption:
- Data Transmission Security: If the data exchanged between IoT devices and servers is not encrypted, it can be intercepted and read by malicious actors during transmission, thus jeopardizing user privacy.
- Insufficient Storage Security: Data stored on IoT devices is often not encrypted, making it vulnerable to theft if the device is compromised.
4. Device Vulnerabilities:
- Poor Software and Firmware Updates: Many IoT devices do not receive regular updates or patches, leaving them vulnerable to exploitation of known security flaws.
- Insecure Design: Some devices may have inherent design flaws or use outdated protocols that do not apply modern security practices.
5. Network Security Issues:
- Botnet Formation: Compromised IoT devices can be co-opted into botnets (e.g., Mirai botnet), which perform distributed denial-of-service (DDoS) attacks and other malicious activities.
- Insecure Network Protocols: Many IoT devices use insecure communication protocols, increasing the likelihood of packet sniffing and replay attacks.
6. Lack of User Control:
- Limited User Awareness: Users may not be fully aware of what data is being collected by IoT devices, how it is being used, or how to manage their privacy settings.
- Difficulties in Data Deletion: Once data is collected, it may be challenging for users to delete or control the lifetime of that data.
7. Inter-Device Communication Risks:
- Device Impersonation: Without proper authentication and authorization mechanisms, a malicious device can impersonate a legitimate device, leading to unauthorized access and control.
- Information Leakage: In scenarios where devices communicate directly with one another, sensitive information can be accidentally exposed to unintended recipients.
8. Regulatory Challenges:
- Compliance Issues: With varying regulations across regions (e.g., GDPR in Europe), manufacturers may struggle to comply with privacy laws, further complicating user privacy and data security.


Comments
Post a Comment