Unit-3
In networking, addressing is crucial for the identification and communication between devices. There are three primary types of addresses: Physical, Logical, and Port addresses. Here’s an explanation of each, along with examples:
1. Physical Address
- Definition: A physical address, also known as a MAC (Media Access Control) address, is a hardware address that uniquely identifies a device on a local network segment. This address is assigned by the manufacturer and is embedded in the network interface card (NIC).
- Format: It is usually represented in hexadecimal format, consisting of 6 bytes (48 bits), typically displayed as six pairs of hexadecimal digits separated by colons or hyphens (e.g.,
00:1A:2B:3C:4D:5E). - Example: If a computer's NIC has a MAC address of
00:1A:2B:3C:4D:5E, this address is used for communication at the data link layer within a local network.
2. Logical Address
- Definition: A logical address is an address that is assigned by the network layer and is used for routing packets across different networks. The most commonly used logical address in IP networks is the IP address, which is designed to identify a device on an IP network.
- Format: An IPv4 address is expressed as four decimal numbers (each ranging from 0 to 255) separated by periods (e.g.,
192.168.1.1). An IPv6 address is represented in hexadecimal format and is longer, consisting of eight groups of four hexadecimal digits (e.g.,2001:0db8:85a3:0000:0000:8a2e:0370:7334). - Example: A device with an IP address of
192.168.1.1can communicate over the Internet or local networks, allowing for logical identification beyond local segments.
3. Port Address
- Definition: A port address is a numerical identifier in a network protocol used to differentiate multiple services or applications running on a single device. Port numbers are associated with specific protocols used for communication and allow multiple services to run on a single IP address.
- Format: Port numbers are expressed as 16-bit numbers, ranging from
0to65535. Standard ports are defined for various services (e.g., HTTP typically uses port80, and HTTPS uses port443). - Example: For a web server running on a device with an IP address of
192.168.1.1, the service can be accessed usinghttp://192.168.1.1:80. Here,80is the port number that specifies the HTTP service.
IPv6 addressing can be represented in several notations, which help in the efficient representation and understanding of the 128-bit addresses. Here are the different notations used for IPv6 addresses:
1. Full Notation
- Description: The full notation is a complete representation of an IPv6 address consisting of 128 bits, divided into eight groups of four hexadecimal digits. Each group is separated by colons.
- Example: An IPv6 address in full notation might look like:
2001:0db8:0000:0042:0000:8a2e:0370:7334
2. Compressed Notation
- Description: Compressed notation simplifies IPv6 addresses by removing leading zeros in each group and replacing consecutive groups of zeros with a double colon (
::). However, this compression can only be used once in any given address to avoid ambiguity. - Example: The above address can be compressed to:
2001:db8:0:42:0:8a2e:370:7334
And if there are multiple consecutive zero groups (e.g., 2001:0db8:0000:0000:0000:0000:0000:0001), it can be further compressed to:
2001:db8::1
3. Mixed Notation
- Description: Mixed notation is used when an IPv6 address is combined with an IPv4 address. This is useful for transitioning from IPv4 to IPv6. It represents the last 32 bits of the IPv6 address as an IPv4 address.
- Example: An IPv6 address that encapsulates an IPv4 address might look like:
::ffff:192.168.1.1
Here, ::ffff: indicates that it is an IPv4-mapped IPv6 address.
4. Embedded Address Notation
- Description: In some situations, IPv4 addresses can be embedded directly into an IPv6 address. This notation is often used for communication between IPv6 and IPv4 networks.
- Example: An IPv6 address with an embedded IPv4 address can be represented as:
The transition from IPv4 to IPv6 is crucial due to the exhaustion of IPv4 addresses and the need for improved features offered by IPv6. Several methods facilitate this migration, each with its advantages and limitations. Here are the primary methods used in transitioning from IPv4 to IPv6:
1. Dual Stack
- Description: This method allows devices to run both IPv4 and IPv6 simultaneously. Dual-stack hosts and routers are configured to support both protocols, enabling communication over either address type.
- Advantages: Flexible and allows gradual transition; existing IPv4 applications can continue functioning while introducing IPv6.
- Limitations: Increased complexity in network management; requires more resources to maintain both protocols.
2. Tunneling
- Description: Tunneling encapsulates IPv6 packets within IPv4 packets so that they can travel over IPv4 networks. Two common tunneling techniques are 6to4 and Teredo.
- 6to4: Automatically creates IPv6 addresses based on the IPv4 address and allows IPv6 packets to be sent over an IPv4 infrastructure.
- Teredo: Provides IPv6 connectivity to nodes behind NAT (Network Address Translation) devices by encapsulating IPv6 traffic within IPv4 User Datagram Protocol (UDP).
3. Translation
- Description: This involves translating IPv4 packets to IPv6 packets and vice versa. The most common protocol used for this is Network Address Translation 64 (NAT64).
- Advantages: Allows IPv6-only clients to communicate with IPv4 servers without needing dual-stack implementations.
- Limitations: Potential for performance issues and complexity in handling certain protocols since not all IPv4 features map directly to IPv6.
Explanation of One Method: Dual Stack
Dual Stack is perhaps the most straightforward and widely adopted method for transitioning from IPv4 to IPv6. In a dual-stack environment, network devices (like routers and servers) have both IPv4 and IPv6 addresses, allowing them to handle traffic for both protocols.
- Implementation:
- Network administrators configure devices to support both IPv4 and IPv6 protocols. This can typically be achieved through standard network configuration practices.
- Each device on the network can be assigned both an IPv4 address and an IPv6 address, enabling it to communicate with clients and servers on either network.
- Operational Advantages:
- Flexibility: Organizations can adopt IPv6 at their own pace while still supporting existing IPv4 infrastructure.
- Backward Compatibility: Applications that depend on IPv4 can continue to run without modification while new applications can be developed to use IPv6.
- Challenges:
- Resource Management: Running a network that supports both protocols requires additional planning, configuration, and resource allocation.
- Complexity: Troubleshooting and managing a dual-stack environment can be more complicated than managing a single protocol.
The Hypertext Transfer Protocol (HTTP) is a fundamental protocol used in the World Wide Web. It governs the communication between web clients (such as browsers) and web servers. Here’s a detailed overview of HTTP, its structure, functionalities, and various features:
1. Overview of HTTP
- Definition: HTTP is an application-layer protocol designed for transferring hypertext (web pages) across the Internet. It defines how messages are formatted and transmitted, and what actions web servers and clients should take in response to various commands.
- Foundation of the Web: It is the basis for data communication on the web and works as a request-response protocol.
2. Working of HTTP
- Client-Server Model: HTTP operates on a client-server model where a client (web browser) sends a request to a server, which then responds with the requested resource.
- Stateless Protocol: HTTP is stateless, meaning each request from a client to a server is treated as an independent transaction. The server does not retain any information about previous requests.
3. HTTP Methods
HTTP defines several methods (also known as verbs) that indicate the desired action to be performed on the specified resource, including:
- GET: Requests data from a specified resource. It is used to retrieve information without causing any side effects.
- POST: Sends data to the server, typically used for submitting forms or uploading files.
- PUT: Updates or creates a resource with the data provided in the request.
- DELETE: Removes the specified resource from the server.
- HEAD: Similar to GET but retrieves only the headers and not the actual resource body.
4. HTTP Request Structure
An HTTP request typically consists of:
- Request Line: Contains the HTTP method, the URL (Uniform Resource Locator) of the resource, and the HTTP version (e.g.,
GET /index.html HTTP/1.1). - Headers: Key-value pairs that provide additional information about the request (e.g.,
User-Agent,Accept, andContent-Type). - Body: Contains data sent to the server (used mainly with POST and PUT methods).
5. HTTP Response Structure
An HTTP response contains:
- Status Line: Includes the HTTP version, a status code indicating the result of the request (e.g.,
200 OK,404 Not Found), and a reason phrase. - Headers: Provide meta-information about the response (e.g.,
Content-Type,Content-Length). - Body: Contains the requested content or data (such as an HTML page).
The Domain Name System (DNS) is a crucial component of the internet infrastructure that plays an essential role in how users interact with online resources. Here are the key reasons highlighting the necessity of DNS:
1. Human-Friendly Naming
- Simplifies Navigation: DNS translates human-readable domain names (like www.example.com) into IP addresses (like 192.0.2.1), which are the numerical addresses used by computers to communicate over the internet. This abstraction allows users to access websites using easily memorable names instead of complex numerical addresses.
2. Distributed Database
- Scalability: DNS is a hierarchical and decentralized system that distributes the responsibility for resolving domain names across many servers worldwide. This design enhances scalability, allowing it to handle billions of queries and domains without a single point of failure.
- Load Distribution: By distributing the DNS system across multiple servers, it reduces the load on individual servers, improving performance and reliability.
3. Dynamic Updates
- Flexibility in Management: DNS records can be easily updated, allowing organizations to change their website IP addresses or implement new services without requiring end-users to remember new addresses. This feature is particularly useful for businesses that frequently update their services or change hosting providers.
4. Email Routing
- Facilitates Email Delivery: DNS is also essential for directing email traffic. It defines mail exchangers (MX records) which specify the servers responsible for receiving email on behalf of a domain. Without DNS, email would not reach its intended destination since users would have to know the IP address of the mail server directly.
5. Enables Subdomain Management
- Organizational Structure: Organizations can create subdomains (like support.example.com or blog.example.com) to organize their web presence more effectively. DNS facilitates this hierarchical structure by allowing easy management of subdomains under a primary domain.
6. Implementation of Security Measures
- DNS Security Extensions (DNSSEC): Enhances the security of DNS by providing an additional layer of trust through cryptographic signatures. This prevents attacks such as cache poisoning, where malicious actors redirect users to fake websites.
7. Load Balancing and Failover
- Improved Reliability: DNS can be configured to provide multiple IP addresses for a single domain, enabling load balancing across multiple servers. This setup can enhance redundancy by allowing for failover in case one server goes down.
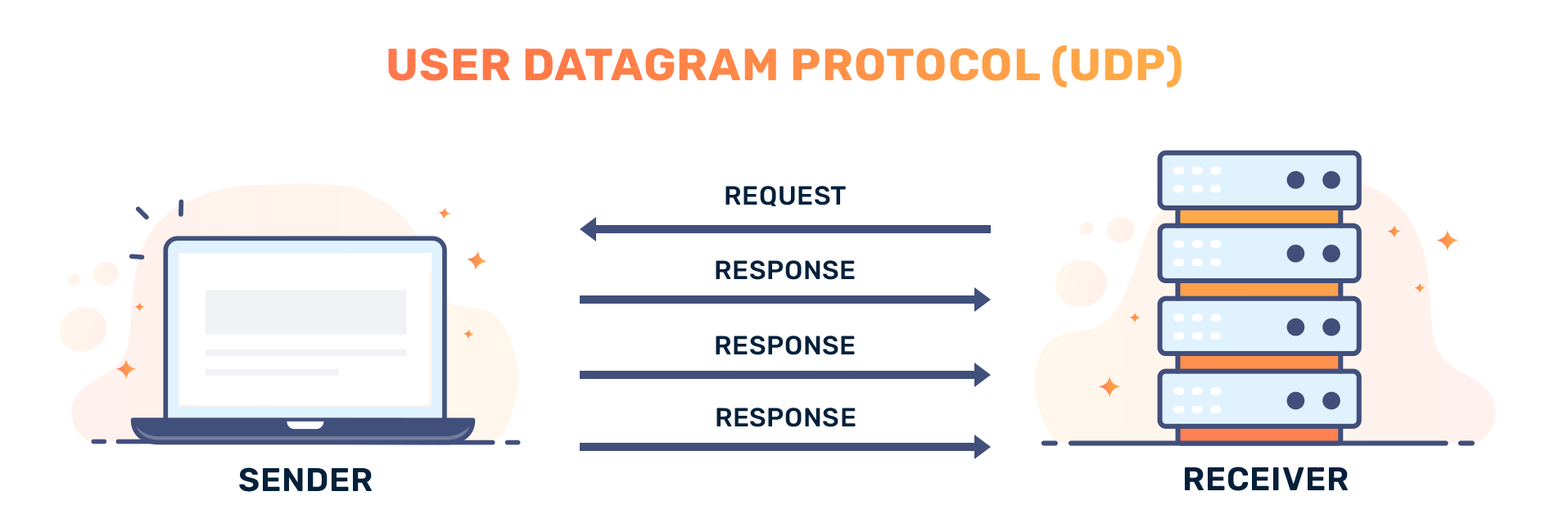
The User Datagram Protocol (UDP) is a communication protocol used primarily for establishing low-latency and loss-tolerating connections between applications on the internet. UDP is part of the Internet Protocol suite, and it is an alternative to the Transmission Control Protocol (TCP). Below are the key features and the format of User Datagram Protocol:
Key Features of UDP:
-
Connectionless Protocol: UDP does not establish a connection before sending data and does not guarantee delivery. This makes it faster than TCP but with the trade-off of reliability.
-
Unreliable Delivery: There is no guarantee that packets sent using UDP will arrive at the destination. There’s no acknowledgment system for received packets.
-
Low Overhead: Because it lacks features such as connection establishment, sequencing, and error recovery, UDP has lower overhead compared to TCP, making it suitable for applications where speed is critical.
-
Multicast and Broadcast Support: UDP supports multicast and broadcast transmission, making it ideal for applications like video streaming and online gaming where messages need to be sent to multiple receivers simultaneously.
-
Simple Message Structure: The UDP header is much simpler than that of TCP, enhancing performance for applications that require minimal latency.
The Network Layer is the third layer in the OSI model and plays a crucial role in managing the delivery of packets across a network. It is responsible for logical addressing, routing, and forwarding of packets. Below are the primary services provided by the Network Layer:
1. Logical Addressing
- The Network Layer provides logical addressing mechanisms, which allows devices on different networks to communicate. Each device is assigned a unique IP address that distinguishes it from other devices within the network. This is different from the physical addressing done at the Data Link Layer, which deals with MAC addresses.
2. Routing
- Routing is a key function of the Network Layer that determines the best path for data packets to travel from the source to the destination across interconnected networks. Routers use routing algorithms and protocols (like RIP, OSPF, and BGP) to facilitate this process and adapt to network changes.
3. Packet Forwarding
- Once the path has been determined, the Network Layer forwards packets from one router to the next along this path. Each router examines the destination address of incoming packets and forwards them accordingly, ensuring that they arrive at the correct destination.
4. Fragmentation and Reassembly
- The Network Layer is responsible for breaking down larger packets (fragmentation) into smaller ones that can be transmitted over various network types, which may have different maximum transmission units (MTUs). At the destination, the fragments are reassembled into the original packet.
5. Traffic Control
- This involves managing the data flow to prevent congestion in the network. The Network Layer may implement methods to regulate the size of packets and the rate of transmission to maintain optimal performance and minimize packet loss.
6. Quality of Service (QoS)
- The Network Layer can offer Quality of Service mechanisms to prioritize certain types of traffic. This is particularly important for applications that require stable and predictable performance, such as video conferencing and online gaming. QoS mechanisms help allocate bandwidth and reduce latency for high-priority packets.
7. Connectionless Communication
- The Network Layer operates in a connectionless manner, meaning that packets are sent without establishing a dedicated end-to-end connection prior to sending data. This service enhances performance and reliability for applications where speed is critical, although it does not guarantee delivery.
IPv4 addressing is an essential aspect of network communication, and it uses several notations to represent IP addresses. Here are the different types of notations used in IPv4 addressing, along with examples:
1. Dotted Decimal Notation
- The most common notation used for IPv4 addresses is dotted decimal notation, where the address is represented as four decimal numbers separated by dots. Each decimal number represents an 8-bit byte (or octet).
Example:
An IPv4 address like 192.168.1.1 consists of four octets:
- 192
- 168
- 1
- 1
2. Binary Notation
- IPv4 addresses can also be represented in binary format, where each octet is expressed as an 8-bit binary number.
Example:
The address 192.168.1.1 in binary is:
- 11000000.10101000.00000001.00000001
3. Hexadecimal Notation
- While less common, IPv4 addresses can also be expressed in hexadecimal format. Each octet is represented as a two-digit hexadecimal number.
Example:
The address 192.168.1.1 in hexadecimal would be:
- C0.A8.01.01
4. CIDR Notation (Classless Inter-Domain Routing)
- CIDR notation is a compact representation that specifies the IP address followed by a slash and the prefix length, which indicates the number of bits in the subnet mask that are used for the network part of the address.
Example:
The address 192.168.1.1 with a subnet mask of 255.255.255.0 can be written in CIDR notation as:
192.168.1.1/24
5. Decimal Notation
- Each octet of an IPv4 address can be expressed as a single decimal number ranging from 0 to 255, representing the 32-bit IP address as a single integer value.
Example:
The address 192.168.1.1 can also be represented in decimal notation as:
- 3232235777 (This is calculated by converting each octet into binary and combining them into a single 32-bit number.)
The architecture of the World Wide Web (WWW) is based on a client-server model and encompasses various components that work together to facilitate access to information and services over the Internet. Here’s an overview of the key elements of the WWW architecture:
1. Clients
- Web Browsers: The primary interface for users to access the web. Examples include Chrome, Firefox, Safari, and Internet Explorer. Browsers interpret HTML, CSS, and JavaScript to display web pages and render multimedia content.
- User Agents: These are any software applications that retrieve and present information from the web, including browsers and mobile apps. They send requests to web servers based on user interactions.
2. Web Servers
- Hosting: Web servers store, process, and serve content to clients. They host websites, which consist of various resources such as HTML documents, images, videos, and scripts. Examples include Apache, Nginx, and Microsoft IIS.
- Response Handling: When a client sends a request (typically via HTTP or HTTPS), the server processes the request, retrieves the requested content, and sends back a response to the client.
3. Hypertext Transfer Protocol (HTTP)
- Protocol: HTTP is the foundational protocol used to transfer data across the web. It defines how messages are formatted and transmitted, as well as how web servers and browsers should respond to various requests.
- Secure Version: HTTPS (HTTP Secure) provides an encrypted connection, ensuring secure data transmission between the client and server, especially important for sensitive information.
4. Uniform Resource Identifier (URI)
- URLs: Each resource on the web is identified by a Uniform Resource Locator (URL), which specifies the location of the resource on the server and the protocol needed to retrieve it. A URL consists of several parts, including the protocol (http or https), the domain name, and the resource path.
Example:
https://www.example.com/index.html
https: Protocolwww.example.com: Domain name/index.html: Resource path
5. HTML, CSS, and JavaScript
- HTML (Hypertext Markup Language): The standard markup language used to create web pages. It structures content by defining elements such as headers, paragraphs, links, images, and other multimedia.
- CSS (Cascading Style Sheets): Used for styling and layout of web pages. CSS controls the appearance of HTML elements, including colors, fonts, and spacing.
- JavaScript: A scripting language that enables interactive elements on web pages. JavaScript allows for dynamic content updates, user interactions, and asynchronous requests to servers (using technologies like AJAX).
6. Databases
- Many web applications rely on databases for storing, retrieving, and managing data. Databases work behind the scenes to serve dynamic content based on user requests.
- Common database systems include MySQL, PostgreSQL, MongoDB, and others that manage data storage and querying.
7. Content Delivery Networks (CDN)
- CDNs are distributed networks of servers that cache content close to users to improve access speed and reduce latency. They serve static resources like images, stylesheets, and scripts, ensuring faster delivery and efficient load balancing.
8. Search Engines
- Search engines are specialized systems that index content from across the web, allowing users to search for information easily. They use complex algorithms to rank and retrieve web pages based on relevance to user queries.
Tunneling in IPv6 addressing is a critical technique used to facilitate the transition from IPv4 to IPv6. This method allows IPv6 packets to be transmitted over an IPv4 network by encapsulating them within IPv4 packets. Below are the reasons for tunneling and an explanation of its functionality:
Reasons for Tunneling in IPv6 Addressing
- Transition Mechanism:
- As organizations and service providers migrate from IPv4 to IPv6, many existing networks still operate on IPv4. Tunneling enables IPv6 packets to traverse IPv4 networks during this transition period, ensuring compatibility and uninterrupted service.
- Interoperability:
- Tunneling allows IPv6 devices to communicate with other IPv6 devices over an IPv4 infrastructure, facilitating the interoperability between IPv4 and IPv6 without necessitating a complete overhaul of existing networks.
- Gradual Migration:
- Many organizations may not be ready to fully switch to IPv6 due to costs or logistical challenges. Tunneling provides a gradual migration path where IPv6 can be implemented without requiring all parts of the network to be upgraded simultaneously.
- Deployment Flexibility:
- Tunneling offers flexibility in deploying IPv6 in environments where IPv4 infrastructure is still prevalent. It allows ISPs and enterprises to begin using IPv6 without having to replace their entire network infrastructure at once.
- Enhanced Features of IPv6:
- By using tunneling, organizations can take advantage of the advanced features of IPv6—such as improved security, larger address space, and better support for mobile devices—while still maintaining their existing IPv4 infrastructure.
How Tunneling Works
- Encapsulation:
- The IPv6 packet is encapsulated within an IPv4 packet. During this process, a new IPv4 header is added to the front of the IPv6 packet. The original IPv6 packet becomes the payload of the IPv4 packet.
- Transmission:
- The encapsulated packet is then transmitted over the IPv4 network. Routers in the IPv4 network only see the outer IPv4 header and handle the packet as they would any other IPv4 traffic.
- Decapsulation:
- Once the encapsulated IPv4 packet reaches its destination, the receiving device (which could be an IPv6-capable router) removes the outer IPv4 header, revealing the original IPv6 packet. This packet can then be processed as normal by the IPv6-enabled device.
- Types of Tunneling Mechanisms:
- Several tunneling protocols exist, including:
- 6to4: Automatically configures IPv6 addresses for sites connecting through the IPv4 Internet.
- Teredo: Allows IPv6 connectivity for hosts behind NAT devices.
- ISATAP (Intra-Site Automatic Tunnel Addressing Protocol): Enables IPv6 communication across an IPv4 intranet.
Static and dynamic routing are two fundamental approaches to routing data packets in computer networks. Each method has its own advantages and disadvantages, making them suitable for different network scenarios.
Static Routing
- Definition:
- Static routing involves manually configuring the routes in a router's routing table. The routes do not change unless a network administrator manually modifies them.
- Configuration:
- Network administrators define specific paths for traffic to follow. This can be done using router command-line interfaces or management software.
- Characteristics:
- Predictability: Since routes are static, they do not change unless altered by a human. This ensures a predictable routing path.
- Simplicity: Static routes are easier to configure in small networks where the topology does not change frequently.
- No Overhead: There is minimal resource usage since static routes do not require ongoing computation or communication between routers. As a result, they do not use bandwidth to exchange routing updates.
- Advantages:
- Control: Network administrators have precise control over routing paths, which can lead to optimized performance for specific applications.
- Security: Static routes can be more secure as they are less susceptible to malicious changes unless access to the router is compromised.
- Disadvantages:
- Scalability Issues: In large or frequently changing networks, maintaining static routes can become cumbersome and error-prone as changes need to be manually updated in multiple routers.
- Failure Handling: If a link goes down, static routing does not automatically reroute traffic unless manually configured to do so. This can lead to network downtime.
Dynamic Routing
- Definition:
- Dynamic routing uses algorithms and protocols to automatically determine the best path for data to travel through a network. Routers communicate with one another to share route information and update their routing tables automatically.
- Protocols Used:
- Common dynamic routing protocols include:
- RIP (Routing Information Protocol): A distance-vector protocol that uses hop count as a routing metric.
- OSPF (Open Shortest Path First): A link-state protocol that calculates the shortest path using various metrics.
- EIGRP (Enhanced Interior Gateway Routing Protocol): A hybrid protocol that combines features of both distance-vector and link-state protocols.
- BGP (Border Gateway Protocol): Used for routing between autonomous systems on the internet.
- Characteristics:
- Automatic Updates: Routers dynamically learn about the network topology and automatically update their routing tables as topology changes occur.
- Load Balancing: Dynamic routing protocols can reroute traffic based on network congestion, link failures, or other factors, allowing for optimal use of available bandwidth.
- Advantages:
- Scalability: Dynamic routing is well-suited for larger networks because it automatically adjusts to changes in the network topology.
- Fault Tolerance: If a link goes down, dynamic routing protocols can quickly find alternative routes, reducing downtime.
- Disadvantages:
- Complexity: Dynamic routing is generally more complex to configure and manage than static routing, requiring a good understanding of networking principles.
- Resource Usage: Dynamic routing protocols can consume more resources, including CPU and memory on routers, and may generate overhead due to routing updates being sent across the network.
Hypertext
Definition: Hypertext is a system of managing and linking text in a non-linear way, allowing users to navigate from one piece of information to another through embedded links. This functionality is fundamental to the World Wide Web, where a user can click on hyperlinks to access related documents or sections of text.
Key Features:
- Links: Hypertext allows users to click on highlighted words or phrases (hyperlinks) to jump to other texts, which can be within the same document or in different documents.
- Non-Linear Navigation: Unlike traditional linear text, hypertext allows users to navigate freely and non-sequentially, enhancing user engagement and content exploration.
Hypermedia
Definition: Hypermedia extends the concept of hypertext by integrating various types of multimedia elements, such as images, audio, video, and text, all interconnected through hyperlinks. Hypermedia allows for a rich multimedia experience on the web.
Key Features:
- Multimedia Elements: Incorporates various types of media (text, audio, video, animations) to present information, making it more interactive and engaging.
- Facilitates Learning: Hypermedia is particularly useful in educational contexts, allowing users to explore complex subjects through various mediums.
Web Client
Definition: A web client is any application that accesses the resources of the World Wide Web. The most common example is a web browser, which retrieves web pages from servers and displays them to users.
Key Features:
- User Interface: Web clients provide a graphical user interface (GUI) that allows users to interact with web content easily.
- Communication: Web clients communicate with web servers using protocols like HTTP/HTTPS to request and receive information.
URL (Uniform Resource Locator)
Definition: A URL is a reference or address used to access resources on the Internet. It provides a specific location for web pages and other resources, enabling web clients to retrieve them.
Structure of a URL: A typical URL has the following structure:
- Protocol: Indicates the communication protocol used (e.g., HTTP, HTTPS, FTP).
- Domain Name: The human-readable address of the server (e.g., www.example.com).
- Path: The specific location of the resource on the server (e.g., /folder/page.html).
- Query String: Optional parameters sent to the server for dynamic content (e.g., ?id=123).
Example:
A complete URL looks like this: https://www.example.com/folder/page.html?id=123.
Unicast Routing
Definition: Unicast routing is a method of sending data packets from a single source to a single destination device over a network. In this type of routing, the data packet is addressed to one specific device, which is identified by its unique IP address.
Key Features:
- One-to-One Communication: Unicast facilitates direct communication between a sender and a receiver, ensuring that the packet reaches its intended recipient without any duplication.
- Efficient Resource Use: Since packets are sent only to the intended recipient, unicast routing is often more bandwidth-efficient for point-to-point communication.
Main Features of the IPv6 Protocol
- Expanded Address Space:
- IPv6 uses a 128-bit address scheme, allowing for a significantly larger number of unique IP addresses (approximately 340 undecillion addresses) compared to IPv4's 32-bit address scheme. This expansion accommodates the growing number of devices connected to the Internet.
- Simplified Addressing:
- IPv6 addresses are represented in hexadecimal notation and are divided into eight groups, making them easier to read and manage. The address structure supports aggregation, which simplifies routing.
- Improved Header Efficiency:
- The IPv6 header has been streamlined by removing optional fields present in IPv4 and reorganizing the structure, which enhances both processing efficiency and routing. The fixed length of the header (40 bytes) simplifies packet handling.
- Enhanced Security:
- IPv6 was developed with security in mind. It includes built-in support for IPsec (Internet Protocol Security) to provide confidentiality, authentication, and data integrity.
- Better Support for Quality of Service (QoS):
- IPv6 introduces the Flow Label field, which helps identify and prioritize packets for real-time services (such as voice and video), allowing for better Quality of Service compared to IPv4.
- Efficient Routing:
- The addressing structure in IPv6 allows for better route aggregation and reduces the size of routing tables, improving the efficiency of network routing protocols.
- Stateless Address Autoconfiguration (SLAAC):
- IPv6 allows devices to configure their own IP address automatically without the need for a DHCP server, simplifying network management and device connectivity.
- No More Network Address Translation (NAT):
- With the large address space of IPv6, NAT is not necessary, allowing for direct end-to-end communication without address translation.
Improvements over IPv4
- Address Exhaustion:
- IPv4 faces a limit on the number of available addresses, which has led to shortages and the need for NAT. IPv6 resolves this problem with a vastly larger address space.
- Routing Efficiency:
- IPv6 offers more hierarchical routing, which helps reduce the size of routing tables compared to IPv4, leading to faster routing and less complexity.
- Integrated Security:
- While IPv4 can incorporate security measures like IPsec, it is optional. In contrast, IPv6 has security features built into its protocol architecture, promoting comprehensive security practices.
- Improved Network Configuration:
- IPv6 simplifies network configuration with features like SLAAC that allow devices to join a network more seamlessly compared to the DHCP model predominantly used in IPv4 networks.
- Quality of Service Capabilities:
- The Flow Label in IPv6 enables better QoS management, which is increasingly important for applications like VoIP and streaming services that require consistent data delivery.
Concept of End-to-End Communication in the Transport Layer
End-to-End Communication: The end-to-end principle in the transport layer of the OSI model refers to a design philosophy that emphasizes the connection between the source and destination hosts in a network. It ensures that data transmission occurs directly between applications running on these hosts, without intermediary entities altering the data content. This principle allows for the implementation of features such as reliability, flow control, and error recovery directly at the transport layer.
Key Aspects of End-to-End Communication
- Direct Interaction:
- The transport layer facilitates communication sessions directly between end-user applications (e.g., web browsers, email clients), enabling applications to manage their own connections and data without needing intermediaries to participate in the process.
- Data Encapsulation:
- Data is encapsulated into transport layer segments with source and destination port numbers, which helps identify the communicating applications on the respective hosts.
- Independence from Network Layers:
- The transport layer operates independently from the underlying network layers, meaning that it does not concern itself with how data is routed through the network. This independence allows for flexibility in various network technologies.
Ensuring Reliable Data Transfer
Transport layer protocols, particularly the Transmission Control Protocol (TCP), use various mechanisms to ensure reliable data transmission:
- Segment Numbering:
- Each data segment is assigned a sequence number, which allows the receiving end to detect any missing segments and reassemble the data in the correct order.
- Acknowledgment (ACK):
- The receiving host sends back acknowledgment messages for received segments. For instance, when a sender transmits a segment, it waits for an acknowledgment from the receiver before sending the next segment. If the sender does not receive an acknowledgment within a predetermined time (timeout), it retransmits the segment.
- Flow Control:
- Transmission Control Protocol (TCP) employs flow control mechanisms to prevent overwhelming the receiver. The receiver informs the sender about the amount of buffer space it has available through a "window size," ensuring that the sender adjusts the data transmission rate accordingly.
- Error Detection and Correction:
- Each segment includes a checksum that allows the receiver to check for errors during transmission. If the checksum does not match, the segment is considered corrupted and is discarded. The sender will subsequently retransmit the lost or erroneous segments.
- Connection Establishment and Termination:
- TCP uses a three-way handshake process to establish a connection (SYN, SYN-ACK, ACK), ensuring both ends are ready for data transfer. This process ensures that both hosts are in agreement regarding communication parameters. Similarly, the connection is terminated in an orderly manner, preventing data loss.
- Retransmission:
- If segments are lost or corrupted, TCP provides mechanisms for retransmission, ensuring that the final data received by the destination is complete and accurate.
User Datagram Protocol (UDP) in Computer Networks
User Datagram Protocol (UDP) is one of the core protocols of the Internet Protocol Suite, used primarily for transmitting data over a network. Unlike TCP (Transmission Control Protocol), which is connection-oriented and reliable, UDP is a connectionless and lightweight protocol that offers several distinct characteristics.
Key Features of UDP
- Connectionless:
- UDP does not establish a connection before sending data. There is no need for a handshake or session setup, which reduces latency in communication. This makes UDP suitable for applications where speed is critical and where occasional data loss is acceptable.
- Unreliable Delivery:
- UDP does not guarantee that data packets (datagrams) will be delivered, nor does it ensure that they will arrive in the same order they were sent. There are no acknowledgment messages, and lost packets are not retransmitted. This lack of reliability can lead to data loss, making UDP suitable for applications where real-time data is more important than accuracy.
- Low Overhead:
- The header of a UDP packet is only 8 bytes, which is significantly smaller than TCP's header (which can be 20 bytes or more). This smaller size reduces the overhead, allowing for faster transmission of data. The simplicity of UDP’s design results in quicker processing and lower resource consumption.
- Datagram Orientation:
- UDP transmits data in discrete units called datagrams, each of which is independent and can be sent without prior knowledge of other packets. Each datagram contains the necessary addressing information (source and destination ports) for routing.
- Multiplexing and Demultiplexing:
- UDP supports multiplexing and demultiplexing, allowing multiple applications to send and receive data through a single IP address using different port numbers. Each application can be uniquely identified using its assigned port, enabling efficient communication.
Use Cases for UDP
UDP is commonly used in scenarios where speed and low latency are essential and where some data loss does not detract from the overall user experience, such as:
- Streaming Media: Applications like video and audio streaming services (e.g., Netflix, Spotify) use UDP to deliver consistent playback without buffering delays.
- Online Gaming: Real-time games utilize UDP for quick data transmission to maintain responsiveness.
- Voice over IP (VoIP): Services such as Skype and Zoom utilize UDP for call data to reduce latency and ensure calls remain smooth.
- Domain Name System (DNS): DNS queries commonly use UDP to resolve domain names quickly without the overhead of a connection.
Role of HTTP in Web Communication
Hypertext Transfer Protocol (HTTP) is the foundation of data communication on the World Wide Web. It is an application-layer protocol designed for transferring hypertext requests and information on the internet. HTTP enables web browsers (clients) to communicate with web servers, facilitating seamless access to web content, including text, images, videos, and other multimedia resources.
Key Functions of HTTP
- Request and Response Model:
- HTTP operates using a request-response model where a client (typically a web browser) sends a request to a server, and the server responds with the requested resource or data. This model is fundamental to how users interact with web applications and websites.
- Stateless Protocol:
- HTTP is considered a stateless protocol, meaning each request from a client to a server is treated as an independent transaction. The server does not retain any information about previous requests, ensuring simplicity and scalability. This characteristic helps optimize performance but necessitates alternative methods (e.g., cookies, sessions) for maintaining state between transactions.
- Methods and Status Codes:
- HTTP defines various methods (such as GET, POST, PUT, DELETE) that specify the action the client wants to perform on the server. Additionally, the protocol uses status codes in responses to convey the status of the request (e.g., 200 OK for successful requests, 404 Not Found for missing resources).
- Content-Type Management:
- HTTP headers allow clients and servers to specify the type of content being transmitted. The
Content-Typeheader indicates the media type (such as HTML, JSON, or JPEG), allowing the client to properly interpret and render the received data.
- Secure Communication:
- When combined with Transport Layer Security (TLS/SSL), HTTP becomes HTTPS (Hypertext Transfer Protocol Secure), ensuring encrypted communication between the client and server. This is essential for protecting sensitive data, such as login credentials and financial information.
Functioning in a Client-Server Model
In the client-server model, HTTP plays a pivotal role by defining how clients and servers communicate over the internet:
- Client Initiation:
- When a user wants to access a webpage, their web browser acts as the client by sending an HTTP request to the appropriate server. This request typically includes the HTTP method (GET for retrieving a resource), the URL of the requested resource, and additional headers that provide context about the request (like user-agent and accept headers).
- Server Processing:
- Upon receiving the request, the web server processes it, retrieves the requested resource (e.g., an HTML file), and prepares an HTTP response. The server includes a status code and headers along with the resource to provide additional information about the response.
- Response Delivery:
- The server sends the HTTP response back to the client, which includes the requested content (such as the HTML of a webpage) and a corresponding status code. The client then interprets the response based on the content type and renders the webpage for the user to view.
- Subsequent Requests:
- If the webpage contains links to other resources (such as images or stylesheets), the browser will send additional HTTP requests for each resource needed, continuing the client-server communication process until all elements are loaded.
Functions of the Transport Layer
The transport layer is a critical component of the OSI model and the Internet Protocol Suite. It is primarily responsible for facilitating end-to-end communication between devices on a network. The key functions of the transport layer include:
- Segmentation and Reassembly:
- The transport layer divides large messages into smaller segments before sending them over the network. Once the segments reach the destination, the transport layer on the receiving end reassembles them into the original message. This process helps manage data efficiently and ensures that large amounts of data can be transmitted without overwhelming the network.
- Connection Control:
- The transport layer can establish, maintain, and terminate connections between applications. Depending on the protocol (such as TCP), it can provide either connection-oriented communication (which establishes a connection before transmitting data) or connectionless communication (which does not establish a prior connection).
- Flow Control:
- To prevent the sender from overwhelming the receiver with data faster than it can process, the transport layer implements flow control mechanisms. This ensures that the sender adjusts its data transmission rate based on the ability of the receiver to accept data, thereby avoiding buffer overflow and improving overall communication reliability.
- Error Detection and Recovery:
- The transport layer is responsible for detecting errors in transmitted segments and ensuring data integrity. It achieves this through methods such as checksums, acknowledgments, and sequencing. In the case of lost or corrupted segments, the transport layer can retransmit the affected segments, ensuring that the application receives accurate data.
- Multiplexing and Demultiplexing:
- The transport layer supports multiple applications running concurrently on a single device by using different port numbers to distinguish between them. This multiplexing allows multiple connections to share the same network resources, and demultiplexing ensures that incoming segments are directed to the appropriate application based on their port number.
- Reliable Data Transfer:
- For protocols like TCP, the transport layer provides reliable data transfer by ensuring that segments are delivered without errors, in sequence, and with no duplicates. This reliable service is essential for applications where data integrity and order are critical, such as file transfers and web page downloads.
- Quality of Service (QoS):
- The transport layer can provide different levels of service quality, such as prioritizing certain types of traffic (like real-time audio or video) to ensure low latency and minimal delay. This QoS management is important for applications that require specific performance levels to function properly.
Unit 3 (3 Marks Questions)
Ans:
Disadvantages of IPv4:
- Limited Address Space: IPv4 uses a 32-bit address, which provides around 4.3 billion addresses, but due to the growth of devices, it is insufficient.
- Address Exhaustion: Due to the rapid increase in internet-connected devices, IPv4 addresses are nearly exhausted.
- Lack of Security: IPv4 does not have built-in security features like encryption and authentication.
- Complex Network Configuration: It relies on NAT (Network Address Translation) due to address shortages, which increases complexity.
- Inefficient Routing: Subnetting and classful addressing lead to inefficient use of address space.
How IPv6 Overcomes These Issues:
- Larger Address Space: IPv6 uses a 128-bit address, providing approximately 340 undecillion (3.4 × 10³⁸) unique addresses.
- Eliminates NAT: Due to abundant addresses, each device can have a unique global IP, removing the need for NAT.
- Built-in Security: IPv6 includes IPSec for encryption and authentication.
- Simplified Addressing and Configuration: Uses autoconfiguration (SLAAC) to assign addresses without DHCP.
- Improved Routing Efficiency: IPv6 simplifies routing tables and reduces overhead.
IPv4 addresses can be represented in multiple notations:
-
Dotted Decimal Notation: The most commonly used format, where the 32-bit address is divided into four 8-bit octets, separated by dots.
- Example: 192.168.1.1
-
Binary Notation: Each octet is represented in 8-bit binary form.
- Example: 11000000.10101000.00000001.00000001 (for 192.168.1.1)
-
Hexadecimal Notation: Each octet is converted into a two-digit hexadecimal number.
- Example: C0.A8.01.01 (for 192.168.1.1)
-
Octal Notation: Each octet is written in base-8 format.
- Example: 0300.0250.0001.0001 (for 192.168.1.1)
-
Classless Inter-Domain Routing (CIDR) Notation: Used for subnetting, where the address is followed by a slash and subnet mask length.
- Example: 192.168.1.1/24
a. 70.45.201.10 ✅ (Valid)
- Each octet is between 0-255.
b. 11100010.23.14.67 ❌ (Invalid)
- The first octet (11100010) is in binary, whereas others are in decimal. IPv4 should be in a consistent format.
c. 101.56.045.78 ❌ (Invalid)
- 045 (octal notation) is not allowed in IPv4. Octets should be in decimal.
d. 211.34.7.8.20 ❌ (Invalid)
- IPv4 addresses should have 4 octets; this has 5.
Stop and Wait ARQ (Automatic Repeat reQuest) Protocol
- A reliable data transmission protocol where the sender transmits a single frame and waits for an acknowledgment (ACK) before sending the next frame.
- If the ACK is not received, the sender retransmits the frame.
Sequence and Acknowledgment Numbers
- Sequence Number (SN): Identifies each transmitted frame uniquely.
- Acknowledgment Number (AN): The receiver sends this to confirm the receipt of a frame.
- Example:
- Sender sends Frame 0 (SN = 0).
- Receiver sends ACK 1 (AN = 1), indicating it expects Frame 1 next.
- If the ACK is not received, the sender retransmits Frame 0.
User Datagram Protocol (UDP)
- Connectionless, lightweight transport layer protocol.
- Does not provide error checking, flow control, or retransmissions.
- Fast but unreliable (used when speed is more important than reliability).
Characteristics:
- No handshake (unlike TCP).
- Packet loss is possible (no retransmission mechanism).
- Minimal overhead (small packet headers).
- Used in real-time applications (e.g., VoIP, video streaming, DNS).
Example:
- When you stream a video, UDP sends packets continuously without waiting for acknowledgments, ensuring a smooth experience.
Since IPv6 is not backward compatible with IPv4, transition mechanisms are needed:
1. Dual Stack
- Devices run both IPv4 and IPv6 simultaneously.
- Can communicate with both IPv4 and IPv6 networks.
- Requires more resources, as both protocols must be maintained.
2. Tunneling
- Encapsulates IPv6 packets inside IPv4 packets to travel over IPv4 networks.
- Useful for ISPs and businesses transitioning gradually.
- Example: 6to4 Tunneling (automatic tunneling method).
3. NAT64 (Network Address Translation IPv6-to-IPv4)
- Allows IPv6-only devices to communicate with IPv4-only devices by translating packets.
- Works like traditional NAT, mapping IPv6 addresses to IPv4.

Comments
Post a Comment